Sent: February 9th, 2005 8:20 PM
|
Safe Sex on the internet?
Sent: February 9th, 2005 8:20 PM
|  |
|
Margaret asked:
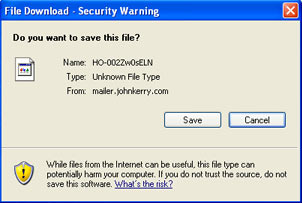
Joe, Is this correct? Be aware. VERY IMPORTANT WARNING Please Be Extremely Careful especially if using internet mail such as Yahoo, Hotmail, AOL and so on. This information arrived this morning from Microsoft and Norton. Please send it to everybody you know who accesses the Internet. You may receive an apparently harmless email with a ... " and it blathered on and on about how Norton and such could not detect it and named a file to be very afraid of. And I answered: This is undoubtedly one of those "self-inflicted" virus infections that is simply a ploy intended to get people to dump their address books. I highly advising going to either the Norton or the McAfee websites and looking at the viruses that are running around. Their descriptions are very clear, and they have dozens of dedicated people on staff - McAfee calls theirs the "Anti-Virus Emergency Response Team (AVERT)" - with nothing better to do than follow and map the evolution of these problems. My own advice at this point in history is this: never open anything that anyone sends to you, unless it is plain text. Period. Point blank. No matter who they are. And before you go to a link someone sends to you, set your browser's security high enough that it prompts you if anything on the page tries to pull a fast one on you, like run a script, execute an application, or load content from another domain. And keep your OS and application software totally up-to-date with security patches and your browser's security settings for the internet set "high" enough that downloads cannot happen without prompting, scripts cannot execute without prompting and pop-ups or pages that spawn new windows are blocked. And turn off the "preview pane" in your email program. And for that matter, dump McAfee and Norton entirely and then download and install Grisoft's AVG excellent free antivirus software and set it to update and scan nightly, in that order! And then get rid of those spyware toolbars from Yahoo and Google that are supposed to may your web browser work better! This is a total pain in the ass, as it makes the web quite tedious to navigate (if you have set your security high enough to feel safe to me, you can't just click on the links that Google presents anymore - you have to right-click them and chose to open them in a new window with your mouse), but that is a minor inconvenience compared to the nightmare of ridding your system of the nasty programs once they infest you. Adware is like getting crab-lice. Spyware is like getting the clap. And the funny part is that these things I am blocking are NOT necessarily bad things for a web-page to be doing. Nearly everything I build for the web has to run scripts of one sort or another to make the customer happy. And I really believe that loading content from across domains is a great way to provide a simple mechanism that allows site owners to update parts of their website without giving them access to areas of the server, or even the site, where they can really break anything. And I may very well send you some HTML email, cuz it is too cool not to pass along, if I really think you can deal with it. But lookat that image I posted above. that came from my security system reporting a file that was trying to download from the link that came in a message from something called mailer.johnkerry.com an organization that I was supposed to trust enough to send money. The most recent internet scourge on the net has been spyware and adware, which executes directly off web-pages unless you have your operating system totally patched. the Most obnoxious form of adware appears to be tens of thousands of zombie machines that once infected with adware have now become unwitting spam-servers. Prior to this crap, the most dangerous files running around the internet have been clearly executable files with the extensions .exe, .zip, .scr, .vbs and .doc files passed from user to user via email. These are dangerous because they can auto-execute and exploit features of the operating system that were intended to make the computer easier for people to use. But these files have to be passed from person to person, and proper hygiene goes along way in preventing their spread. The more sophisticated means that the hackers have been using lately use a rather old trick called remote exploitation of a buffer overflow vulnerability. This clever attack sort of dissolves your OS 's defenses and creates a backdoor that allows code to execute on your machine. Lately, at least since late last December, some clever folks have figured out how to exploit both Windows Media Player and iTunes to execute evil on the machines of people who download music. And the code executes after the buffer overflow can be almost anything since playlists have pretty broad access to system resources. If it can write to your hard drive to update the database on your hard-drive to include artist and track information about the CD you are playing, it can probably be coaxed into writing whatever it wants to write. Wherever it wants to write it. Think about the implications of this for a minute. Mac users have operated in a blissful bubble for a few years, thinking that they were exempt from this crap, believing in the elegance of the Mac OS and the tooth fairy, I suppose. They were wrong of course, and this vulnerability has been well known and well documented within the security community for the past couple of years. I am convinced that the reason the Mac has been spared this misery to date is that there were simply not enough users to justify developing malware to attack them. But that the recent "major-league hit" status of iTunes/iPod and the arrogance of the users has apparently offended the gods at last. Here is a timeline for the first instance of the iTunes buffer overflow vulnerability problem initiated from a playlist file on the Mac: 12/17/2004 Initial vendor notification 12/17/2004 Initial vendor response 01/13/2004 Public disclosure So far, Microsoft's antispyware Beta looks like a very interesting tool, and I have it installed if only for the system explorer applications it provides. So far, these applications especially the Windows Shell Execution Hooks viewer seem to go beyond the tools that were included in XP's task manager, and the other process monitors available in XP or NT4 or at least provide a better integrated interface for them. And yes, I do recognize that Microsoft XP is probably the best documented spyware application in history and yes, am learning to write for Firefox ... I assume that a lot of this is funded by the bushies, who watched the internet play a significant role in the past election and have seen several instances where it has almost exposed their malfeasance over the past few years, and who I believe would rather the internet went away entirely, or at least who would certainly rather that you and I went away. Therefore, I do not expect the situation to get better right away. |